*Cryptolocker image via http://blog.malwarebytes.org*
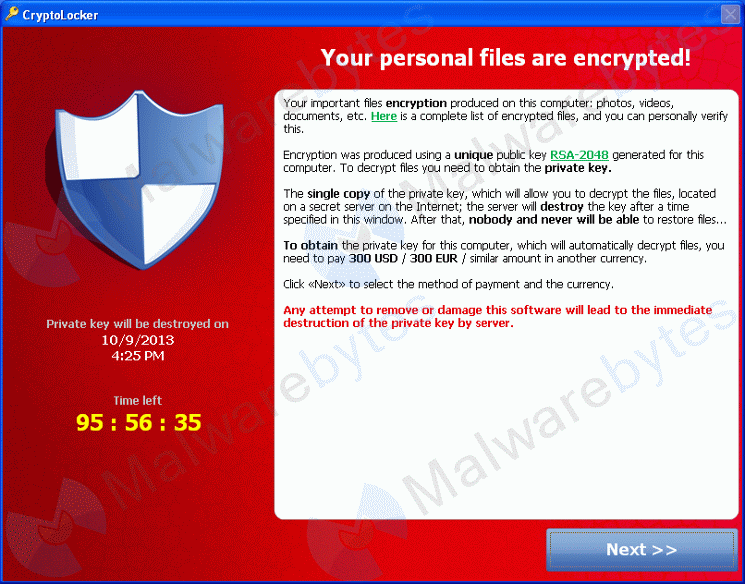
CryptoLocker is a kind of malicious software that is referred to by many as “RansomWare” because that is descriptive of what it does when you become infected, it holds your files for ransom.
This software is nasty and has infected millions of computers around the world, encrypting their files and demanding money to decrypt them. Up to this point in time you must be running a version of MS Windows to ‘catch’ this infection.
To quote CMIT solutions : CryptoLocker
“…takes hold in a variety of ways: after a user clicks on a link or attachment in a spam email; via exploit kits on hacked websites; or through Trojans that pretend to be required programs to view online videos. Once installed, CryptoLocker scans a computer’s local and network drives, encrypts over 50 different file types, and then demands anywhere from $100-$300 to de-encrypt them.”
I will cover some of the measures that you can take to try and prevent this infection but there is one thing we should do first. Go make a backup of your computer/server right now.
Back it up to something that can be removed or disconnected from your machine after the backup is made. Once the backup is finished remove/disconnect the device. If your computer or server can see it, CryptoLocker can encrypt it. Imagine for just a moment how difficult it would be to replace all of your business data.
Once that is done, what can you do to deal with this problem?
1. Avoidance
- Never open any attachments from any sender. Yes, period – until you confirm the authenticity of the attachment do not open it. CryptoLocker will send an email that pretends to be someone/some company that you know. Fedex, UPS, DHS…etc. Even if they are PDF files do not open them without confirmation.
- I know that none of us go to these sites but I have to say it. CryptoLocker uses ‘online video viewer’ Trojan programs to spread itself. Places that make you download a ‘viewer’ should be avoided.
- Another difficult thing to do but important, is to use something to manage your web browser’s ability to run any scripts without your consent. NoScript or something like it. Time consuming but a good safety measure. CryptoLocker uses hacked web sites to exploit vulnerabilities on your computer to install itself.
- Hover your mouse over links in any email. Do not click on it. Hovering will allow you to preview the actual link, not the text that calls the link. If it looks odd, stay away. If it is from a company that you know, Amazon, Microsoft, etc. and you want to go to the written link – type the address into your browser by hand rather than clicking on it in the email.
2. Plan ahead.
- Make online backups. There are offerings from some of the ‘cloud’ based backup companies might meet your needs. Contact them and ask them if your backup using their service would be protected from something like CryptoLocker. Don’t use software that makes the ‘cloud drive’ part of your visible file system since if it is visible CryptoLocker can encrypt it.
- Make local backups in a way that give access to the backup device only while the backup is being made. Use a device that is not susceptible to being infected after it is disconnected (i.e. not another windows computer).
This is a brief article and I have attempted to cover a lot of information quickly. Do some more research to make yourself comfortable. If you subscribe to an antivirus software, check and see if it can help with protecting you from the infection as opposed to just being able to clean the virus after you are infected. Call someone you know in the industry and get their advice. Or, you could even contact your local, friendly IT company. (Hint hint)
Don’t be afraid – just be prepared.