06
Feb 2015
Throwback Thursday: The Oregon Trail
In this, our inaugural journey through the oiled gears and dimly glowing vacuum tubes of our technologies past, we revisit an old friend. This companion not only shaped our collective understanding of a very important part of American history, it also instilled a generation with a healthy fear of both snake bites and dysentery. This week, we roll our wagon west and test our mettle against the Oregon Trail. Sitting
by 2bridges CIO, Ken Lombardi Don’t worry. The sky is not falling, but after we heard of this problem 2bridges Technologiesthought it was a important enough that we write a blog post to make our clients aware. Due to the level of access to your personal information this exploit allows it is a good idea to patch this on your android device as soon as possible. As our mobile devices
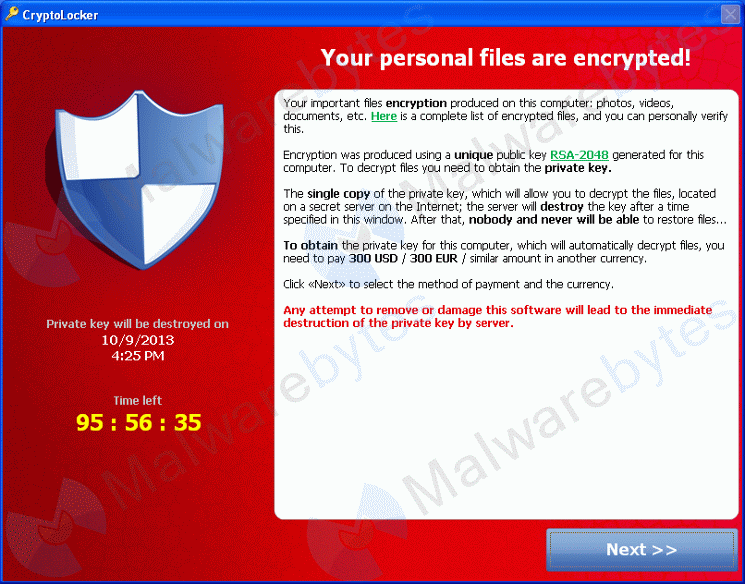
*Cryptolocker image via http://blog.malwarebytes.org* CryptoLocker is a kind of malicious software that is referred to by many as “RansomWare” because that is descriptive of what it does when you become infected, it holds your files for ransom. This software is nasty and has infected millions of computers around the world, encrypting their files and demanding money to decrypt them. Up to this point in time you must be running a
19
Sep 2013
New from 2bridges: The Managed Private Cloud
Cloud Computing. More and more, this ominous phrase creeps into news sites, tech blogs, and even the occasional forum used for sharing captioned kitten pictures. A quick Google image search gives the impression of a multitude of electronic devices shooting arrows of information back and forth between a shared amorphous blob. Today’s blog is not so much about explaining in depth how this colloquially called collection of connected computers works,
19
Aug 2013
2bridges visits 3R Technology in Seattle
2bridges went up to Seattle to visit with Computer/Hardware recycling and environmentally conscious 3R Technology. 3R Technology has been smashing hardrives, destroying data and soundly recycling potentially hazardous waste that would have otherwise been slated for a landfill since 2003. Our (3R Technology) primary mission is to encourage reuse, the best form of recycling. We live in a technology-abundant region, where access to information and communication is accepted as a
31
Jul 2013
1-2-3-4-5 Password Do’s and Don’ts
2bridges loves security. From bike chains, to combination lockers, to that little sealer thing on the top of ziplock bags. One of the first lines of defense in the digital world is knowing how to correctly select a password. Here are a few quick do’s and don’ts to keep in mind when trying to protect your personal information online: Do use both upper and lower case letters. Do include digits
18
Jun 2013
Replacing a HDD with an SSD
How to replace a HDD to SSD on a MacBook Pro and to upgrade to OS X 10.8.
06
May 2013
Internet Archive
Archive is a documentary focused on the future of long-term digital storage, the history of the Internet and attempts to preserve its contents on a massive scale. Part one features Brewster Kahle, founder of the Internet Archive and his colleagues Robert Miller, director of books, and Alexis Rossi, director of web collections. On a mission to create universal access to all knowledge, the Internet Archive’s staff have built the world’s